Projects

An Online Cost-Efficient Protection Scheme for Quick Recovery in All-Optical WDM Mesh Networks
Designing path-protection based scheme to prevent traffic disruptions from single-link failures. Developing and implementing new algorithms; an improvement over existing algorithms like streams, gives more savings in terms of network resources in dynamic environment. Heuristic gave near-optimal results for networks like USANET, NSFNET.
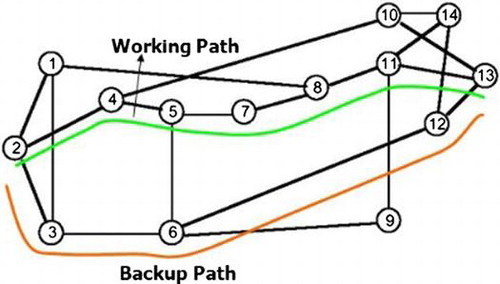
An offline scheme for reducing cost of protection in all-optical WDM mesh networks with fast recovery
Designing schemes to prevent disruption of user traffic from failures in offline mode. Developing and implementing new algorithms; an improvement over existing algorithms like gstream in static environment. Formulation of Integer Linear Program as a mathematical proof of optimal solution.

Developing Robust Machine Learning for deep learning applications
Study of adversarial training, threat models, poisoning, inference and evasion attacks including membership inference, generative adversarial attack (GAN) and its applications in fraud detection, malware classification, etc. Survey of existing attack models, countermeasures and its limitations, finally developing a more robust learning system.

Security Analysis of Unmanned Aerial Vehicles
Analyzed vulnerabilities of drones under study (namely DJI Phantom and Parrot Bebop), performed attacks, programmed some hijacking methods and proposed countermeasures. GPS spoofing based attacks like height hack, force-landing were successfully performed at Nanyang Technological University, Singapore.
